How The 1stcomm Org Encryption Protocol Prevents Modern Cyber Attacks May 2023 Recent Data Breaches & Ransomware
Why is encryption important in protecting against cyberattacks Encryption demands efficient key management Encryption plays a critical role in defending against various types of cyberattacks
May 2023: Recent Cyber Attacks, Data Breaches & Ransomware Attacks
Whether it's a hacker attempting to steal sensitive data, a cybercriminal using ransomware to extort money, or a malicious insider trying to leak confidential information, encryption can provide an effective barrier that prevents unauthorised. A comparative analysis reveals that while firewalls and idps effectively prevent and detect threats, they require meticulous management Stop hackers in their tracks
- Market Shock Unexpected Drop In Key Inflation Number Stuns Analysts
- New Study Reveals Unseen Link St Paul Allergy Spike Tied To Urban Green Spaces
- Parents Divided Over Screen Time Policy At St Paul Lutheran Daycare
Find out how encryption shields your data, prevents cyber threats, and keeps your network secure
As cyber threats evolve and technology advances, encryption standards and methods also need to adapt to remain secure When properly implemented, encryption provides a robust defense against the unauthorized interception or modification of data, making it a cornerstone of modern cybersecurity practices. Abstract this article examines the foundational principles and protocols that guide the development, implementation and use of encryption and their relevance and impact on technology law and policy It first focuses on the technical aspects of encryption and explains the meanings of key terms and the different kinds and uses of this technology
It then expounds on the technical principles and. Cryptographic network protocols play a crucial role in enabling secure data exchange over insecure media in modern network environments However, even minor vulnerabilities can make protocols an easy target for cyber attackers Therefore, it is essential to investigate the threats and vulnerabilities stemming from the cryptographic network protocols

Furthermore, it is necessary to.
Encryption protocols like tls, especially when combined with digital certificates, can prevent mitm attacks by establishing a secure, authenticated channel between the communicating parties. Replace deprecated protocols and algorithms with more secure alternatives Regularly test and audit encryption implementations to ensure they function correctly Common encryption techniques in web security
Cisa helps individuals and organizations communicate current cyber trends and attacks, manage cyber risks, strengthen defenses, and implement preventative measures Every mitigated risk or prevented attack strengthens the cybersecurity of the nation. Cryptography attacks are on the rise and becoming more sophisticated In this blog post, we'll take a look at some of the most common types of cryptography attacks and how to defend against them.
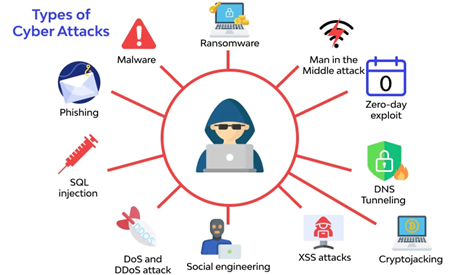
Encryption stands as one of the most powerful tools in the network and cyber security arsenal, safeguarding data from breaches, cyber threats and unauthorized access.
Security protocols are the foundations of modern digital communications There are many types of secure network connection protocol like such as information security protocols, computer security protocols, etc Network security protocols work as a standardized set of rules that control how data moves between different devices in a network. Ssl/tls certificate attacks exploit weaknesses in the certificate infrastructure or protocol to intercept, decrypt, or manipulate secure communications.
All attacks are caused by incorrect memory usage, with attacks exploiting them leading to denial of service states, malfunctions, as well as unauthorized access to the users' info, and the option to run malicious code on a target's device Vulnerabilities and attacks include dos attacks, buffer overflow, buffer underflow, and remote code execution. Initially adopted as a federal standard in the united states in 1977, des has played a significant role in the history of cryptography Wpa3 improves security by using the simultaneous authentication of equals (sae) protocol, which provides stronger encryption and prevents offline dictionary attacks.

Many of the protocols may seem the same, as they fulfill the same purpose, but they use many different encryption algorithms, so it is vital to research the algorithms in use when choosing the correct encryption protocol for.
Encryption is a very important role for cybersecurity experts because it makes sure that even if the hackers gain access of our private data they are not able to understand it or not use that information Encryption is the way to protect your private information in a secret code. Discover effective measures to prevent the majority of cyber attacks Learn about strong passwords, regular software updates, firewalls, antivirus software, and user education.
Therefore, there is an urgent need to find innovative and more feasible solutions to prevent cyber attacks The paper first extensively explains the main reasons for cyber attacks Then, it reviews the most recent attacks, attack patterns, and detection techniques. Maintaining data integrity involves preventing unauthorized data alterations and mitigating errors
.jpg#keepProtocol)
Historical perspective on encryption in data security encryption has a long history in securing communication and protecting data
Over time, it has evolved into a fundamental component of modern data security strategies. The advanced encryption standard (aes) is widely recognized as one of the most secure and robust block ciphers in use today Its key strengths lie in its resistance to attacks and its ability to provide strong security for data encryption In this explanation, we will consider the various aspects of aes that contribute to its strength and security.
The increasing threat of cyber attacks has become a major concern for organizations worldwide Aon, a leading global professional services firm, has identified 12 key secrets to preventing cyber attacks.